
Desktop application sprawl revealed as rules and roles addressed
ITD has approximately 1,550 staff and another 100 contractors who work at the department, using ITD-issued equipment, including PCs, laptops, tablets, and mobile phones. That many technology endpoints can be problematic.
“Each time we bring a new resource into the organization or move a resource (employee or contractor), we repeat the process of identifying what key technology resources the individual requires to be successful in their role,” explained IT Governance and Architecture Manager Tyler Zundel.
“This is redundant work that takes significant effort and varies depending on the supervisor performing the request. In many ways, it creates a custom set of applications, access privileges, and assigned equipment for any given ITD contributor.”
Because of this lack of clarity and business-defined needs, requirements are often missed, causing delays and additional work that consumes valuable resources, and creates low customer satisfaction.
Zundel added that, “To ‘shortcut’ the process, supervisors and managers simply say, ‘make employee X’s system look like employee Y’s’ – a bad practice that often allows staff privileges they don’t need, and creates risks to our sensitive data and information.”
Those issues are exacerbated when you consider there are more than 2,000 unique applications on ITD desktops that are poorly mapped to business functions. Sometimes, there is no knowledge or who or what these applications are used for. Yet, they require technical support, make upgrades problematic, and threaten network integrity. For example, ITD’s network has nine culvert design applications in the environment and we don’t know if all nine are required or if one will suffice.
“Because there are no standard, well-defined resource requirements for technology across the organization, we end up with employees and contractors adding new or otherwise nonstandard hardware or software to the environment under the guise of innovation or improving performance,” Zundel said. “These unmanaged add-ons have made our IT infrastructure and application environment more complex, more difficult and costly to support, and expose us to additional Cyber Security risk.”
A group at the recent Leadership Summit was charged with coming up with a method to learn which applications applied to which user groups, and how to grant access accordingly. The goal was to improve performance of both line-of-business staff and the IT department as a whole by standardizing and reducing complexities that may create a barrier to optimized job performance.
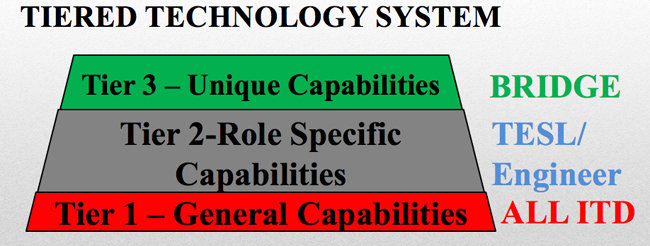
Their solution was a tier-based plan that can be applied to every role in the department:
- Tier 1 would the necessary computing equipment, applications, and system access to cover all employees of ITD.
- Tier 2 is role-specific. For example, if someone in DMV needs access, this is the tier where those needs would be identified.
- Tier 3 is “Unique Capabilities” — the vision is to have a pre-approved list of applications for end users to choose from.
.
In order for an application to be approved, it would go through a review process conducted by a specific group comprised of employees with similar duties responsible for business outcomes that require the capabilities provided by the application. Beyond that, traffic engineers would meet to discuss the programs and benefits and determine which applications would be used. Some of the groups identified are Traffic Engineering, Design/Construction Engineering, Bridge Design, and Materials/Geology.
Zundel, the team facilitator, described the desired future state where “every employee and contractor has a role assignment that clearly defines the technology needs for the role, so that when a new contributor joins ITD, the individual has the technology to be successful on the date of arrival. When an individual changes roles, updates to the individual’s available technology are implemented seamlessly, resulting in the person having what is required, and nothing that is not required. And when an individual leaves the organization, the technology resources are recovered quickly, and any access privileges are revoked in a timely manner to protect our security.”
“This will result in eliminating delays, curtailing variant and non-standard technology, improving service quality, consistently delivering services, and improving customer satisfaction while identifying opportunities for improvement,” he added.
The next step for the team is to get back together after the holidays and create the polling mechanism to identify the Tier 2 applications, and to set the functional “user groups” up with information and requests for paring down the application footprint from their areas. This information will be valuable input to a forthcoming enterprise IT project for Role Based Access, Equipment, and Application management.
Watch the Application Sprawl Team video.

Pictured left to right, bottom to top:
Benjamin Burke, Cecilia Awusie, Stephenie Grover, Scott Stokes, Linda Brown, Sydney Lewis, Chris Victory, Ben Ward, Brian Bannan, Elise Shanks, Darryl Kuhrt, Tyler Zundel, Brock Dille, Alex Deduck
Published 12-22-17